
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Five Steps to Perform a Cloud Risk Assessment
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-13-2016
12:45 PM

The main difficulty in assessing cloud risks is the lack of visibility about the implemented security controls by the cloud provider. Oftentimes customers can see security certification information, but these are not sufficient to have a precise cloud risk assessment. We published a research paper with a practical approach to perform cloud risk assessments, with reproducible steps that potential cloud customer perform:
1 - Define the cloud risk scenarios affecting your business There are relevant cloud-specific risks to watch out for: lock-in (interesting thoughts about this topic appear in this post by fstrimling), compliance challenges, shared technology risks, most of them are discussed in the ENISA recommendations for information security in the Cloud, from 2010, but you will likely add consider other risks affecting your business, such as foreign government espionage, which was not in the ENISA’s enumeration, but became extremely relevant since 2013.
2 - Determine relevant security controls to protect your assets Each risk scenario links to a number of vulnerabilities. In order to mitigate these, one must select appropriate security controls, more often by adopting a security standard. The Cloud Controls Matrix by CSA is a great resource for that. It contains an extensive collection of controls and practices extracted from the most prominent standards. These controls are grouped in relevant categories (called Control Domains), which make it easy to relate to a number of risk scenarios. For instance, the Compliance control domain will help in addressing the “Regulatory” and “Legal” risk scenarios, whereas controls in the Resiliency domain will help to mitigate some risks related to service delivery and quality of service.
3 - Assess your cloud provider The main difference with doing risk assessments in general is that by moving data to the cloud, the organizations do not have the same level of control as on premise. Depending on the delivery model, a considerable part of the responsibilities will rely on the cloud provider. It is important to assess how the provider implements the controls that are relevant to your risk scenarios from step 1. For that, an excellent source of information is the CSA Security, Trust & Assurance Registry (STAR). Each provider in the repository responded to around 300 questions related to the most important information security standards (this is the Consensus Assessments Initiative Questionnaire, CAIQ). As a cloud consumer, your organization needs to know which controls are the most suited to mitigate the threats in your risk scenarios. Ah, the cloud provider you intend to contract is not in the CSA Registry? Just ask them to fill in the CAIQ. Or the answers in the Star Registry aren't clear? Ask for more details to the provider. It has probably already gone through this exercise and they are sharing the answers only under some NDA.
4 - Estimate the residual risks and further measures to be taken Not all responsibilities are on the hands of the provider. There are controls you will need to put in place, even if you are using a SaaS. For example, your employees need to be aware about social engineering attacks. For PaaS and IaaS there are many more security controls to activate and monitor by yourself.
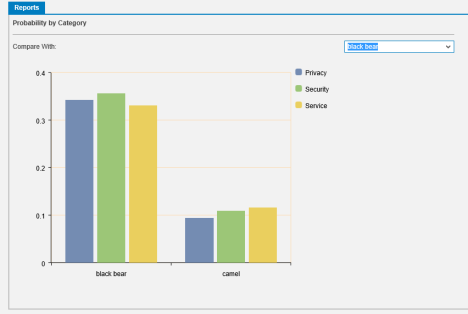
5 - Make your decisionDetermine which data and/or business process will move to the cloud and estimate the impact to your organization to their CIA (confidentiality, integrity, and availability) properties. Different cloud offers will address security needs in different ways. In the paper, we show an approach to cluster risk scenarios in three main risk indicators allowing compare different provi..., a screenshot with pseudonymized providers is given below. Another important point is to review SLAs, privacy policies and further contractual documents very carefully. Finally, once you made your choice, keep in mind that sometimes there is room for negotiating specific contracts terms to obtain better guarantees.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
86 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
270 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,578 -
Product Updates
323 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
395 -
Workload Fluctuations
1
Related Content
- Consuming SAP with SAP Build Apps - Connectivity options for low-code development - part 2 in Technology Blogs by SAP
- explore the business continuity recovery sap solutions on AWS DRS in Technology Blogs by Members
- SAP Cloud Integration: Understanding the XML Digital Signature Standard in Technology Blogs by SAP
- Enhanced Data Analysis of Fitness Data using HANA Vector Engine, Datasphere and SAP Analytics Cloud in Technology Blogs by SAP
- Harnessing the Power of SAP HANA Cloud Vector Engine for Context-Aware LLM Architecture in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 11 | |
| 10 | |
| 10 | |
| 10 | |
| 8 | |
| 7 | |
| 7 | |
| 7 | |
| 7 | |
| 6 |